ESET research shows how malware developers found a way to bypass Google's permission restrictions.
An ESET research shows how malware developers found a way to bypass Google's permission restrictions.
Google restricted the use of "SMS" and "call log" permission groups in March 2019. One of the positive effects is that login stealer apps are no longer able to bypass the SMS-based two-factor authentication (2FA) mechanism.
However, we now discovered malicious Android apps capable of stealing "one-time passwords" (OTPs) from 2FA SMS notification inserts. The malicious apps use it to bypass Google's new permission policies. On top of that, even one-time passwords from 2FA email notifications can be intercepted.
An app we found in the Google Play Store mimics the Turkish cryptocurrency exchange BtcTurk to scam login information for the real platform (phishing attack). Instead of intercepting SMS messages to bypass 2FA protection, malware steals OTP from notification overlay. This one can even hide the malware so that the victim doesn't notice anything about the OTP theft.
This is the first time since the introduction of Google's new policy that we saw such a circumvention of 2FA. ESET security products detect the malware as an Android/fake app.KP.
The malicious phishing apps
Under the developer name "BTCTurk Pro Beta," the fake app was released on 7. June 2019 uploaded to the Google Play Store as "BTCTurk Pro Beta". Since then, more than 50 users already installed the fake app. BtcTurk is a Turkish cryptocurrency exchange whose official app can be accessed via its website – but only for Turkish users.
A second app appeared under the name "BtcTurk Pro Beta" on 11. June 2019 in the Google Play Store. This time under the developer name "BtSoft". Although both appear similar, they seem to be the works of different malware developers. We reported the fake app on 12. June 2019. At this point, the app had been installed on less than 50 devices.
After the app was removed from the Play Store, another one appeared from the same developers under the name "BTCTURK PRO" with the same features. We reported this the following day.
Figure 1 shows the two malicious fake apps as they appeared in the Google Play Store.

Figure 1: Fake BtcTurk apps in the Google Play Store
The new 2FA bypass technique?
Once installed, both fake apps mentioned in the previous section use a similar approach. In the following section, we describe the new 2FA bypass technique using the first app "BTCTurk Pro Beta" as an example.
After the application is launched, it requests notification access, as shown in Figure 2. The permission allows reading notifications displayed by other apps installed on the device.
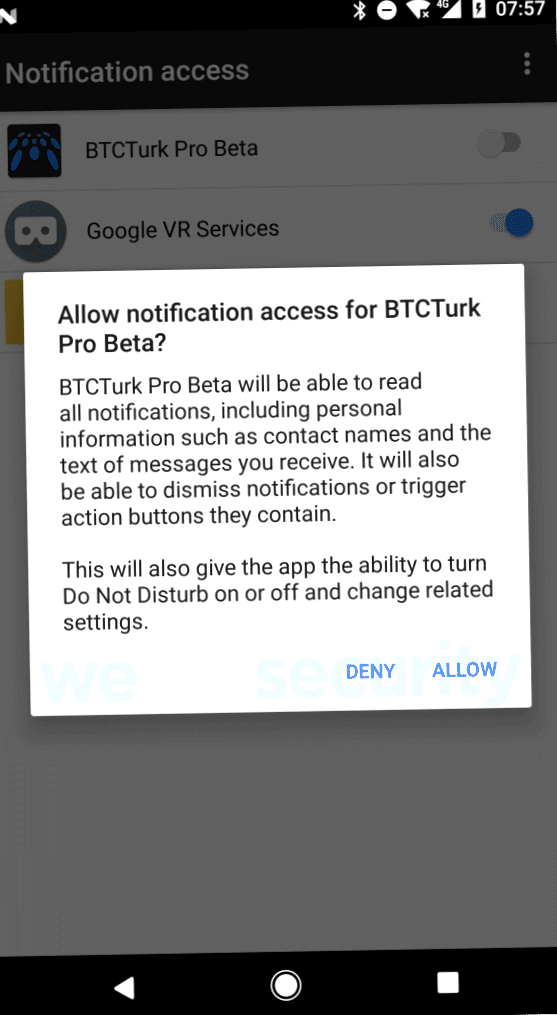
Figure 2: The BTCTurk fake app requests notification access
Notification access has been available to Android users since Jelly Bean version 4.3 available. This means that almost all Android devices can be tricked by this 2FA bypass technique. Both BtcTurk fake app require at least Android version 5.0 (KitKat), which means that approx. 90% of Android devices are covered.
If the user allows access to the notifications, the next step is to show him a phishing form where the BTCTurk login information is to be entered, as shown in Figure 3.
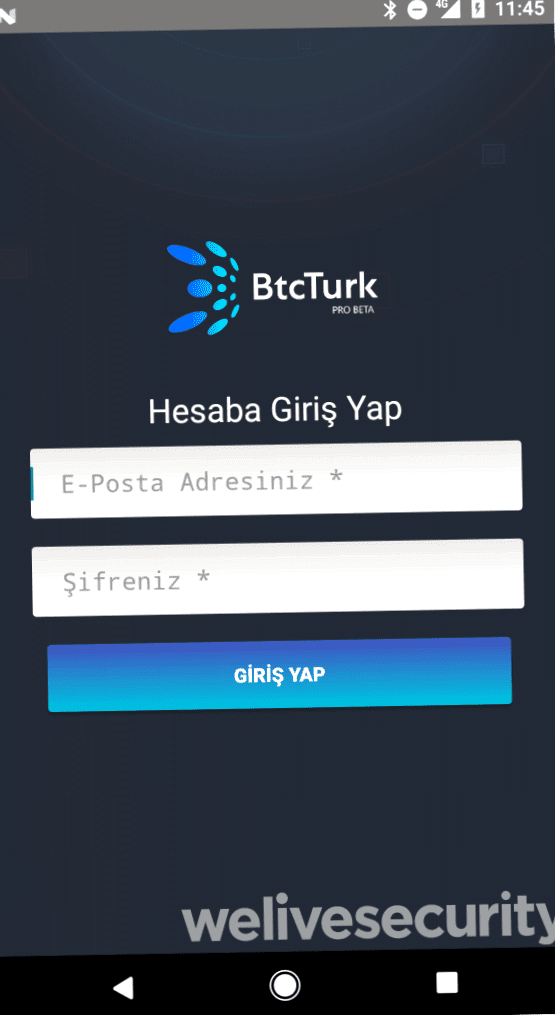
Figure 3: Phishing form of the fake app
After confirming the login information, the fake app displays a Turkish-language error message (Figure 4). Translated, it says something like: "Opss! Due to the changes made in the SMS verification system, we are temporarily unable to maintain our mobile app. You will be informed about the end of the maintenance work via app. Thank you for your understanding."
In the background, the previously entered login information is sent to the attackers' servers.

Figure 4: The error message displayed by the malicious fake app
Thanks to notification access, the phishing app reads notification feeds from other apps, including SMS and emails. Using filters such as "sms, messaging, gm, yandex, mail, k9, outlook," the BtcTurk fake app only grabs certain notifications (Figure 5).
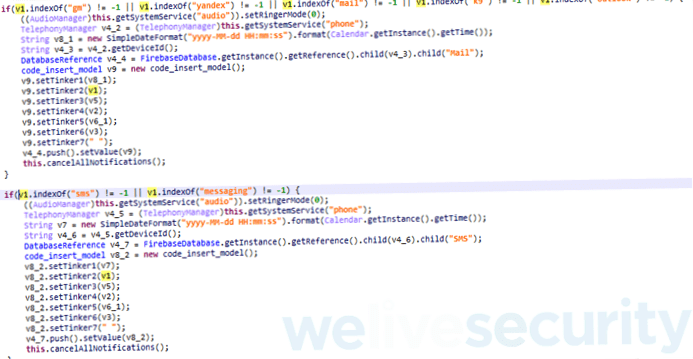
Figure 5: Filtering by targeted app names and types
The displayed notification content of the apps is sent to the malware developers' servers – And this is independent of the notification settings (bspw. Message content hidden in lock screen). Those responsible for the fake apps are also able to hide incoming messages and set the ringtone mode to "mute". In this case, the victim would hardly notice anything about the compromise.
While the fake app are capable of bypassing two-factor authentication (2FA). However, it works only with limitations. The attackers can merely access the text that fits into the notification. For example, this does not guarantee that the one-time password (OTP) is included in it. Based on the targeted apps, we can see that mainly SMS and email messages are of interest to the cybercriminals. SMS-2FA are usually designed to fit the OTP into the notification. With email 2FA, text lengths vary widely, which is why the OTP doesn't necessarily show up in notifications.
A fast-spreading malware technique
Just last week, we analyzed a similar fake app that targeted Turkish crypto exchange Koineks. Thanks to @DjoNn35, we have found out about the malicious application. The Koineks fake app uses the same malware techniques as the above malicious Android apps. However, this is not able to hide messages and mute the mobile device.
According to our analysis, the Koineks fake app comes from the same attackers who created BTCTurk Pro Beta. This shows that malware developers are currently fine-tuning to get the largest number of OTPs possible.

Figure 6: Koineks fake app information in the Google Play Store
How to protect yourself from this danger?
Last month, we warned about the rising bitcoin prices and the accompanying wave of new crypto-malware that would appear in the Google Playstore. This post confirms that cybercriminals are not resting and are looking for new ways to circumvent security measures. They also want to profit from the boom.
Therefore, here we present a few quick tips on how to protect yourself from Finance malware:
- You should only trust the official apps that are linked on the official company websites.
- Login credentials should only be entered into trusted form fields, of impeccable origin.
- Always keeping the Android mobile device up to date (software updates).
- Reputable mobile security apps block and remove many cyber threats.
- Whenever possible, hardware token OTPs or software-based OTPs other than SMS and email should be used.
Installing only trusted apps is especially important when notification access is requested.
Indicators of Compromise (IoCs)
Package nameHashESET detection name
| btcturk.per.beta | 8C93CF8859E3ED350B7C8722E4A8F9A3 | Android/FakeApp.KP |
| com.app.btsoft.app | 843368F274898B9EF9CD3E952EEB16C4 | Android/FakeApp.KP |
| com.app.elipticsoft.app | 336CE9CDF788228A71A3757558FAA012 | Android/FakeApp.KP |
| com.koinks.mobilpro | 4C0B9A665A5A1F5DCCB67CC7EC18DA54 | Android/FakeApp.KP |