Homer ransomware is an application of the Dharma ransomware family. It works by encrypting files to charge a decryption fee. However, developers extort money illegally because in reality they do not have the ability to decrypt files, even the ones they have blocked themselves. All locked files will get the extension ". Homer ". After the final infection, Homer ransomware displays a notice with information about the infection.
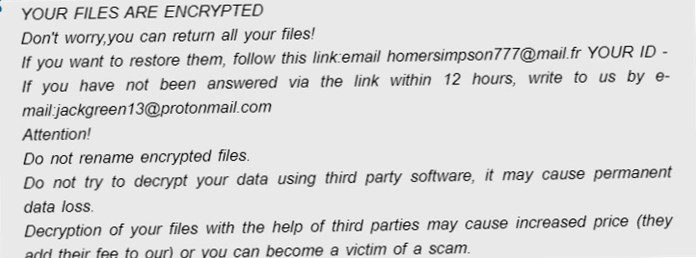
This notice reports file locking and suggests contacting developers via email. If you write to developers, they will offer you to buy special tools for decryption. If users do not receive a response from criminals within twelve hours, they must write to an additional email address. According to developers, if you try to unlock files in any other way. This may result in permanent data loss. In fact, decrypting developers is just a trick to extort money. The only way to return files is to remove the Homer ransomware.
How to remove Homer ransomware
If you have working backups of your encrypted files or do not try to recover lost files, scan your computer with one or more antivirus and anti-malware programs or reinstall the operating system completely.
SpyHunter is a powerful anti-malware solution that protects you from malware, spyware, ransomware and other types of Internet threats. SpyHunter is available for Windows and macOS devices.
Norton (Windows, macOS, iOS, Android) The link may not work properly if your country is currently under sanctions.
However, if you want to try all possible methods to recover encrypted files, including data recovery tools, I suggest you use these tools first and scan with anti-malware later. Skip to the explanation
How to restore files encrypted with Pojie ransomware
If you want to recover files encrypted by ransomware, you can either try to decrypt them or use file recovery methods.
Ways to decrypt the files:
- Contact the ransomware authors, pay the ransom and possibly get the decryptor from them. This is not reliable: they may not send you the decryptor at all, or it may be poorly executed and unable to decrypt your files.
- Wait until security researchers find a vulnerability in the ransomware This will allow you to decrypt files without paying. This turn of events is possible, but not very likely: out of thousands of known ransomware variants, only dozens have been found to be decryptable for free. You can visit NoMoreRansomware website from time to time to see if a free decryptor for GandCrab exists.
- Use paid services for decryption. For example, antivirus provider Dr. Web offers its own decryption services. They are available to users of Dr.Web Security Space and some other Dr. Web products free of charge if Dr. Web installed and running at the time of encryption (More details). For users of other antivirus programs, decryption, if thought possible, costs €150. According to the statistics of Dr. Web, the probability of restoring files is about 10%.
Other ways to restore encrypted files:
- Restore from backup. If you make regular backups on a separate device and check from time to time if they are ok and files can be successfully restored, you will probably have no problems getting your files back. Just scan your computer with some AVs and anti-malware programs or reinstall the operating system and then restore it from backup.
- Restore some files from cloud storage (DropBox, Google Drive, OneDrive, etc.) if you have connected one. Even if encrypted files have already been synchronized with the cloud, many cloud services keep old versions of modified files for some time (usually 30 days).
- Restore volume shadow copies of your files If they are available, ransomware usually tries to delete them as well. Volume Shadow Copy Service (VSS) is a Windows technology that takes regular snapshots of your files and allows you to undo changes made to them or recover deleted files. VSS is activated together with System Restore: It's enabled by default on Windows XP through Windows 8, and disabled by default on Windows 10.
- Use file recovery software. This probably won't work for Solid State Drives (SSD – it's a newer, faster and more expensive type of data storage device), but it's worth a try if you store your data on a hard disk drive (HDD – older and more common storage device so far). If you delete a file from your computer – and I mean completely delete it: Use Shift + Del or empty the recycle bin – on SSD it will be deleted from the drive immediately. However, on HDD it is more likely to be marked as deleted and occupy space on a hard drive – than available for writing, but the data is still there and usually recoverable by special software. However, the more you use the computer, especially if you do something that involves writing new data to the hard drive, the more likely it is that your deleted file will be overwritten and disappear for good. For this reason, in this guide we will try to recover deleted files (as you remember, ransomware creates an encrypted copy of a file and deletes the original file) without installing anything on a hard drive. Just remember that this may still not be enough to successfully recover your files – after all, when ransomware creates encrypted files, it writes new information to a hard drive, possibly in addition to the files it just deleted. This actually depends on how much free space is available on your hard drive: the more free space, the less likely it is that new data will overwrite the old data.
In addition, we need to 1) prevent ransomware from encrypting files we recover when malware is still active; 2) try not to overwrite files deleted by ransomware. The best way to do this is to disconnect your hard drive and connect it to another computer. You can scan all your folders, scan with antivirus programs, use file recovery software or recover data from volume shadow copies. However, it is better to download all the needed tools beforehand and disconnect the computer from the Internet before connecting the infected hard drive, just to be sure.
Disadvantages of this method:
- This may void your warranty.
- For laptops, this is more difficult, and you need a special case (hard drive enclosure) to install a hard drive before connecting it to another computer.
- It is possible to infect the other computer if you open a file from the infected drive before scanning the drive with AVs and removing any malware found. Or if all AVs fail to find and delete the malware.
Another, simpler option is to load into safe mode and perform all file recovery actions from there. However, this means that the hard disk will be used and possibly some data will be overwritten. In this case, it is preferable to use only portable versions of the recovery software (which do not require installation), download them to an external device, and save all recovered files to an external device as well (external hard drive, USB flash drive, CD .). , DVD etc.).
Boot into safe mode:
Windows XP, Windows Vista, Windows 7:
- Restart the computer.
- Once you see a startup screen, tap and hold F8 until a list of options appears.
- Use the arrow keys to select Safe Mode with Network Support.
- Press releases Next.
Windows 8, Windows 8.1, Windows 10:
- Down hold Windows key and hit X key.
- Select shutdown or log off.
- Press releases displacement button and click resume.
- When prompted to select an option, click Advanced Options =>Startup Settings.
- Click Restore in the lower right corner.
- After Windows restarts and offers you a list of options, press F5 select Enable Safe Mode with Network.
Back up your encrypted files
It is always advisable to make a copy of the encrypted files and stow them away. This could help you if a free ransomware decrypter becomes available in the future, or if you decide to pay and get the decrypter, but something goes wrong and files are irreparably damaged during decryption.
Use file recovery tools to restore files
Stellar Windows Data Recovery Professional is a user-friendly Windows data recovery software to recover lost documents, emails, photos, videos and more from hard drive, USB, memory card, etc. recover.